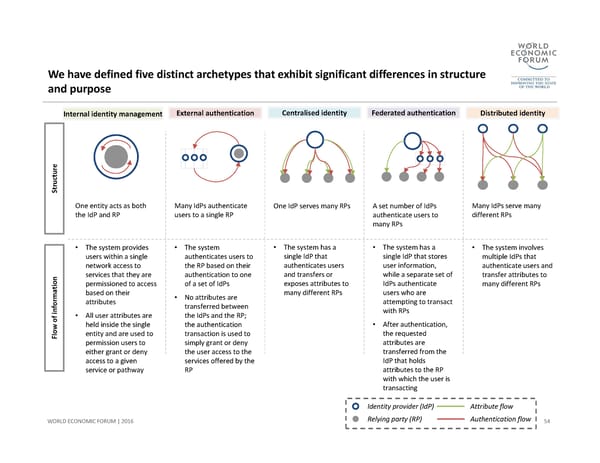
We have defined five distinct archetypes that exhibit significant differences in structure and purpose 54 WORLD ECONOMIC FORUM | 2016 Structure Flow of information Internal identity management •The system provides users within a single network access to services that they are permissioned to access based on their attributes •All user attributes are held inside the single entity and are used to permission users to either grant or deny access to a given service or pathway One entity acts as both the IdP and RP External authentication •The system authenticates users to the RP based on their authentication to one of a set of IdPs •No attributes are transferred between the IdPs and the RP; the authentication transaction is used to simply grant or deny the user access to the services offered by the RP Many IdPs authenticate users to a single RP Federated authentication •The system has a single IdP that stores user information, while a separate set of IdPs authenticate users who are attempting to transact with RPs •After authentication, the requested attributes are transferred from the IdP that holds attributes to the RP with which the user is transacting A set number of IdPs authenticate users to many RPs Centralised identity •The system has a single IdP that authenticates users and transfers or exposes attributes to many different RPs One IdP serves many RPs Distributed identity Many IdPs serve many different RPs •The system involves multiple IdPs that authenticate users and transfer attributes to many different RPsAttribute flowAuthentication flow Identity provider (IdP) Relying party (RP)
 A Blueprint for Digital Identity Page 54 Page 56
A Blueprint for Digital Identity Page 54 Page 56