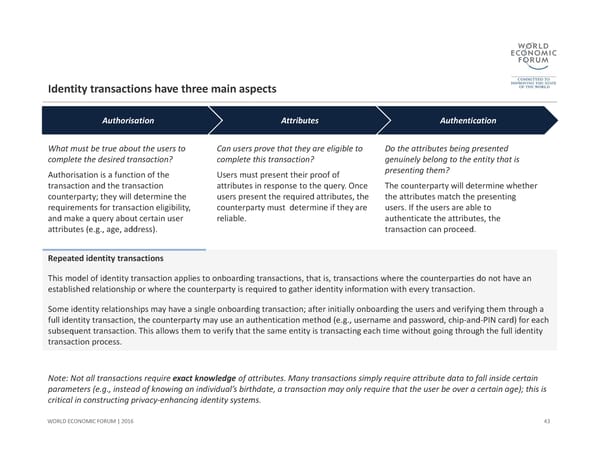
Identity transactions have three main aspects 43 WORLD ECONOMIC FORUM | 2016 Authorisation Attributes Authentication Can users prove that they are eligible to complete this transaction? Users must present their proof of attributes in response to the query. Once users present the required attributes, the counterparty must determine if they are reliable. Do the attributes being presented genuinely belong to the entity that is presenting them? The counterparty will determine whether the attributes match the presenting users. If the users are able to authenticate the attributes, the transaction can proceed. What must be true about the users to complete the desired transaction? Authorisation is a function of the transaction and the transaction counterparty; they will determine the requirements for transaction eligibility, and make a query about certain user attributes (e.g., age, address). Repeated identity transactions This model of identity transaction applies to onboarding transactions, that is, transactions where the counterparties do not have an established relationship or where the counterparty is required to gather identity information with every transaction. Some identity relationships may have a single onboarding transaction; after initially onboarding the users and verifying them through a full identity transaction, the counterparty may use an authentication method (e.g., username and password, chip‐and‐PIN card) for each subsequent transaction. This allows them to verify that the same entity is transacting each time without going through the full identity transaction process. Note: Not all transactions require exact knowledge of attributes. Many transactions simply require attribute data to fall inside certain parameters (e.g., instead of knowing an individual’s birthdate, a transaction may only require that the user be over a certain age); this is critical in constructing privacy‐enhancing identity systems.
 A Blueprint for Digital Identity Page 43 Page 45
A Blueprint for Digital Identity Page 43 Page 45